仮想マシン上(VMware)でMalwareを動かす際の設定
- Malwareには、VMware上で動作していることを検知すると動作しないものが存在する。
- 以下の設定を行うことにより、VMwareの検知機能を回避出来る場合がある。
- 完全では無いので注意!!
参考サイト
vmxファイル(*.vmx)の設定変更
- 仮想マシンのVMware構成ファイル(*.vmx)に以下を追加する。
- VMware Toolsの機能(コピー&ペースト、ファイルのD&D等)が使用出来なくなるため、若干利便性が落ちる。
isolation.tools.getPtrLocation.disable = "TRUE" isolation.tools.setPtrLocation.disable = "TRUE" isolation.tools.setVersion.disable = "TRUE" isolation.tools.getVersion.disable = "TRUE" monitor_control.disable_directexec = "TRUE" monitor_control.disable_chksimd = "TRUE" monitor_control.disable_ntreloc = "TRUE" monitor_control.disable_selfmod = "TRUE" monitor_control.disable_reloc = "TRUE" monitor_control.disable_btinout = "TRUE" monitor_control.disable_btmemspace = "TRUE" monitor_control.disable_btpriv = "TRUE" monitor_control.disable_btseg = "TRUE" monitor_control.restrict_backdoor = "TRUE"
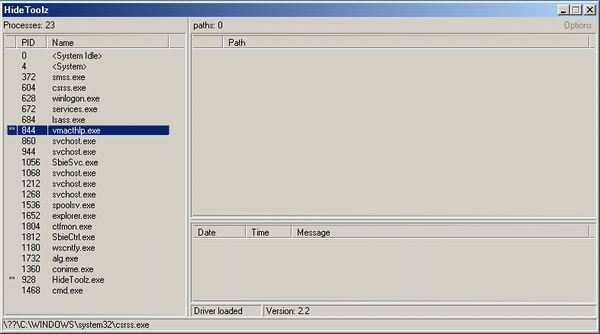
HideToolz (プロセスの隠蔽)
-
- internals - HideToolz.7z
- ウイルス対策ソフトで検知するため取扱注意
- 動作しているプロセスを隠蔽するためのツール
- 表示されたくないプロセス(VMware関連/デバッガ/システム情報ツール等)を指定するだけ。
Hacker Defender rootkit
- 指定したファイル/フォルダ/レジストリ/プロセス等を隠蔽するツール
- 現在は配布されていない
- ウイルス対策ソフトで検知するため取扱注意
- 以下設定ファイル(hide.ini)で hxdef100.exe を実行する
> hxdef100.exe hide.ini
[Hidden Table] hxd* vmu* vmt* vmw* tools* procexp* ollydbg* [Root Processes] hxd* vmu* vmt* vmw* tools* procexp* ollydbg* [Hidden Services] HackerDefender100 vmu* vmt* vmw* procexp* [Hidden RegKeys] VMware, Inc. Sysinternals [Hidden RegValues] vmu* vmt* vmw* [Startup Run] [Free Space] [Hidden Ports] [Settings] Password=infected BackdoorShell=cmd.exe FileMappingName=_.-=[Hacker Defender]=-._ ServiceName=HackerDefender100 ServiceDisplayName=HXD Service 100 ServiceDescription=NT rootkit DriverName=HackerDefenderDrv100 DriverFileName=hxdefdrv.sys [Comments]
参考情報:ScoopyNG - The VMware Detection Tool
- 仮想OS上で、VMware環境か検知するツール
上記3つの対策を施した上で実行した結果
- 「Test 7: VMware emulation mode」で検知されてしまう。
- Derek Soeder's (eEye Digital Security) VMware emulation test
#################################################### :: ScoopyNG - The VMware Detection Tool :: :: Windows version v1.0 :: [+] Test 1: IDT IDT base: 0x8003f400 Result : Native OS [+] Test 2: LDT LDT base: 0xdead0000 Result : Native OS [+] Test 3: GDT GDT base: 0x8003f000 Result : Native OS [+] Test 4: STR STR base: 0x28000000 Result : Native OS [+] Test 5: VMware "get version" command Result : Native OS [+] Test 6: VMware "get memory size" command Result : Native OS [+] Test 7: VMware emulation mode Result : VMware detected (emulation mode detected) :: tk, 2008 :: :: [ www.trapkit.de ] :: ####################################################
特に明示されていない限り、本Wikiの内容は次のライセンスに従います: CC Attribution-Share Alike 4.0 International